PowerShell - Handling passwords.
Of course, passwords should never be stored in plain text in a script file. PowerShell offers possibilities for a secure handling of passwords. As an example, a password for a specific user can be stored encrypted as a text file. Only the respective user can decrypt the file, for other users the file is worthless.
Get-Credential
For entering username and password PowerShell provides the following cmdlet: Get-Credential

PS C:\Users\LiBe> $cred=Get-Credential
cmdlet Get-Credential at command pipeline position 1
Supply values for the following parameters:
Credential
Create PSCredential object and save it to a file
Some cmdlets can use the created PSCredential object directly. If the credentials are needed multiple times, they can of course be stored in a variable, or in a file for a later call:
#generate Authentication Passwordfile:
if (-not (Test-Path "$($env:Temp)\myapp_password.txt")) {
$credential = Get-Credential
$credential.Password | ConvertFrom-SecureString | Set-Content "$($env:Temp)\myapp_password.txt"
}Read PSCredential object from file
To create the PSCredential object from a file we need the user name: Variable $user
$Credential=New-Object -TypeName System.Management.Automation.PSCredential -ArgumentList $user, (Get-Content "$($env:Temp)\myapp_password.txt" | ConvertTo-SecureString)
Save password to a file
The password can also be saved directly to a file without "Get-Credential".
"password" | ConvertTo-SecureString -AsPlainText -Force | ConvertFrom-SecureString | Out-File "$($env:Temp)\myApp_password.txt"The password "password" looks like this in the file:
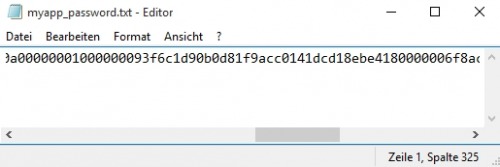
Read password from the file and use it as plain text password:
$SecureCredential = Get-Content "$($env:Temp)\myApp_password.txt" | ConvertTo-SecureString
$UnsecurePassword = (New-Object PSCredential "username",$SecureCredential).GetNetworkCredential().Password ({{pro_count}})
({{pro_count}})
{{percentage}} % positive
 ({{con_count}})
({{con_count}})